^e _rels/.rels ( N0HCn ]&*`QA$F?)8|h*r)j6|)WR`. CybeReadys fully-automated solution makes IT training more efficient and fun for employees. Its really a glorified checklist. The template has space for you to note where the risk is likely to occur, and what kind of risk it might be. Compile and state all the vulnerabilities and, The crux of a good template includes a matrix of risk assessment results featuring the likelihood of different risks occurring, impact analysis, risk rating, existing controls, and alternative controls: these measures could be quantitative, qualitative, or. Keep reading for a detailed overview of cyber risk assessments along with a five-step plan you can use for your own companys cyber risk assessments and a free downloadable risk assessment template. Now you have more control to automate tasks, like alerts for upcoming deadlines, and can even assign individual tasks to team members.  NqAHgj3Ie7Qm PK ! Its not possible to remove all risk. Given the likelihood and impact potential of different risks, you can then start to prioritize these risks based on a straightforward risk matrix. List the participants, the questionnaires, and tools used to carry out the assessment, and describe any risk model used to form the basis of your assessment. On the upper right-hand corner is an import button. 103 0 obj
<>/Filter/FlateDecode/ID[<997E80B51578CA4AB8ECB382798D9154>]/Index[89 24]/Info 88 0 R/Length 82/Prev 381678/Root 90 0 R/Size 113/Type/XRef/W[1 3 1]>>stream
Aside from helping to understand security risks better and reduce adverse business outcomes, an accurate risk assessment ensures you spend your security budget wisely. The calculations from the worksheets make it easy to show raw risk scores and also weighted scores, which take into consideration the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk. Clearly, setting out the scope of the assessment sets out the timeframe it supports, the technological considerations, and the areas of your business that it applies to. Frameworks and threat libraries can prove helpful in identifying all possible threats to your assets; look to sources like CAPEC for more ideas. Learn more about ProjectManager and how it can improve your business, Discover app combinations that improve your productivity, Set milestones, connect dependencies and track progress, Collect and view real-time data on your work for key insights, Manage portfolios, align objectives and get high-level overviews, Generate in-depth, easy-to-read reports to share progress, Prioritize and execute your work with transparency and agility, Organize and manage your tasks to boost team productivity, Share files, add comments, and work together in real-time, Create automated workflows and improve productivity, For individuals or small teams that want to track their work, For small-to-medium teams that need to manage robust projects, For medium-to-large teams that need to optimize portfolios, For organizations that need customized security and priority support, Reduce lead time, ensure quality and perfect your process, Create schedules, manage crews and deliver under budget, Streamline IT processes and scale up with ease, Plan projects, track progress and manage resources, Build comprehensive project plans and organize tasks, Manage backlogs, create workflows and execute sprints, Schedule and assign work to bring your project in on time, Assign resources, balance workload and move forward, Manage your teams, collaborate and track progress, Take control of your work from start to finish, Track your teams time, whether theyre on-site or remote, Learn more about our company and our mission, Join us in transforming how work gets done, Watch video tutorials for ProjectManagers features, Read the industry-leading blog on work management, Get key insights on major topics in project management, Access documentation on using ProjectManager, Accelerate delivery on your next IT project, Keep track of all the phases of your build, Kickoff your next launch with a premade plan, Plan your sprints with out-of-the-box workflows, Make your next marketing campaign a success, Sync work across all your devices and access it on the go. %%EOF
NqAHgj3Ie7Qm PK ! Its not possible to remove all risk. Given the likelihood and impact potential of different risks, you can then start to prioritize these risks based on a straightforward risk matrix. List the participants, the questionnaires, and tools used to carry out the assessment, and describe any risk model used to form the basis of your assessment. On the upper right-hand corner is an import button. 103 0 obj
<>/Filter/FlateDecode/ID[<997E80B51578CA4AB8ECB382798D9154>]/Index[89 24]/Info 88 0 R/Length 82/Prev 381678/Root 90 0 R/Size 113/Type/XRef/W[1 3 1]>>stream
Aside from helping to understand security risks better and reduce adverse business outcomes, an accurate risk assessment ensures you spend your security budget wisely. The calculations from the worksheets make it easy to show raw risk scores and also weighted scores, which take into consideration the importance of the control, the maturity of the protections in place, and any compensating measures that may exist to reduce the risk. Clearly, setting out the scope of the assessment sets out the timeframe it supports, the technological considerations, and the areas of your business that it applies to. Frameworks and threat libraries can prove helpful in identifying all possible threats to your assets; look to sources like CAPEC for more ideas. Learn more about ProjectManager and how it can improve your business, Discover app combinations that improve your productivity, Set milestones, connect dependencies and track progress, Collect and view real-time data on your work for key insights, Manage portfolios, align objectives and get high-level overviews, Generate in-depth, easy-to-read reports to share progress, Prioritize and execute your work with transparency and agility, Organize and manage your tasks to boost team productivity, Share files, add comments, and work together in real-time, Create automated workflows and improve productivity, For individuals or small teams that want to track their work, For small-to-medium teams that need to manage robust projects, For medium-to-large teams that need to optimize portfolios, For organizations that need customized security and priority support, Reduce lead time, ensure quality and perfect your process, Create schedules, manage crews and deliver under budget, Streamline IT processes and scale up with ease, Plan projects, track progress and manage resources, Build comprehensive project plans and organize tasks, Manage backlogs, create workflows and execute sprints, Schedule and assign work to bring your project in on time, Assign resources, balance workload and move forward, Manage your teams, collaborate and track progress, Take control of your work from start to finish, Track your teams time, whether theyre on-site or remote, Learn more about our company and our mission, Join us in transforming how work gets done, Watch video tutorials for ProjectManagers features, Read the industry-leading blog on work management, Get key insights on major topics in project management, Access documentation on using ProjectManager, Accelerate delivery on your next IT project, Keep track of all the phases of your build, Kickoff your next launch with a premade plan, Plan your sprints with out-of-the-box workflows, Make your next marketing campaign a success, Sync work across all your devices and access it on the go. %%EOF
 Here is a brief outline of the sections to expect in a good cyber risk assessment template: In order to effectively manage and respond to cyber risk, you need to determine the potential adverse impacts that can arise in your information ecosystem and the probability of different risks. Our free risk assessment tool is a good start, but youre going to need more help.
Here is a brief outline of the sections to expect in a good cyber risk assessment template: In order to effectively manage and respond to cyber risk, you need to determine the potential adverse impacts that can arise in your information ecosystem and the probability of different risks. Our free risk assessment tool is a good start, but youre going to need more help.  and the areas of your business that it applies to. ProjectManager is a cloud-based tool with online Gantt charts that create plans with phases, linked task dependencies, even calculating the critical path and setting baselines. pN!'h?'!? Since cyber risk assessments are complicated. Thats a lot of money to leave in the sights of potential risk. Use this free It Risk Assessment Template for Excel to manage your projects better. For example, a risk assessment of your web applications should include application data and server infrastructure among the assets. s/g
|ofA_Ar7O,8i\"Z&
1I0pLNFU8ipvqE$e8~Fso^'?.Fopp^vhaC~3
bLO!j24&IfS? Highly motivated and sophisticated threat actors emerge constantly, and growing IT complexity from digital transformation initiatives widens the attack surface.
and the areas of your business that it applies to. ProjectManager is a cloud-based tool with online Gantt charts that create plans with phases, linked task dependencies, even calculating the critical path and setting baselines. pN!'h?'!? Since cyber risk assessments are complicated. Thats a lot of money to leave in the sights of potential risk. Use this free It Risk Assessment Template for Excel to manage your projects better. For example, a risk assessment of your web applications should include application data and server infrastructure among the assets. s/g
|ofA_Ar7O,8i\"Z&
1I0pLNFU8ipvqE$e8~Fso^'?.Fopp^vhaC~3
bLO!j24&IfS? Highly motivated and sophisticated threat actors emerge constantly, and growing IT complexity from digital transformation initiatives widens the attack surface.  These dueling priorities typically result in inefficient use of their time and skills.
These dueling priorities typically result in inefficient use of their time and skills.  Instead of relying on historical occurrences to estimate the probability of different threat events, a better approach combines. Create custom columns, break your tasks into subtasks and toggle easily between the sheet and the Gantt. Our real-time dashboard tracks your progress across several metrics, including time, cost and workload. The template is sort of an outline. Section# 17.03(2)(b) requires companies to identify & assess reasonably-forseeable internal and external risks! RACI stands for responsible, accountable, consulted and informed. This template not only gives you a bucket in which to collect risks to your IT system but actions that will mitigate those risks and the means by which you can monitor your organization so as to know immediately when the rise arises if it does. %PDF-1.5
%
However, some levels of risk arent acceptable because they potentially lead to companies not being able to carry out core functions. v?>EZ6 t4>Q3, A}H
Instead of relying on historical occurrences to estimate the probability of different threat events, a better approach combines. Create custom columns, break your tasks into subtasks and toggle easily between the sheet and the Gantt. Our real-time dashboard tracks your progress across several metrics, including time, cost and workload. The template is sort of an outline. Section# 17.03(2)(b) requires companies to identify & assess reasonably-forseeable internal and external risks! RACI stands for responsible, accountable, consulted and informed. This template not only gives you a bucket in which to collect risks to your IT system but actions that will mitigate those risks and the means by which you can monitor your organization so as to know immediately when the rise arises if it does. %PDF-1.5
%
However, some levels of risk arent acceptable because they potentially lead to companies not being able to carry out core functions. v?>EZ6 t4>Q3, A}H  >]yQ|75w$Oo W3af%a9%i// The following are a few of the many training videos and blog posts weve published on the subject. There are many things it can do to help you get started on assessing the risk in your IT system, but eventually, youre going to hit a wall. Then, you can tag it for priority, and add the start date and planned end date to keep track of its progress. Our latest version of theCybersecurity Risk Assessment Templateincludes: The Excel-based worksheet comes with graphs showing before & after risk levels.
>]yQ|75w$Oo W3af%a9%i// The following are a few of the many training videos and blog posts weve published on the subject. There are many things it can do to help you get started on assessing the risk in your IT system, but eventually, youre going to hit a wall. Then, you can tag it for priority, and add the start date and planned end date to keep track of its progress. Our latest version of theCybersecurity Risk Assessment Templateincludes: The Excel-based worksheet comes with graphs showing before & after risk levels. 

 We even give you a completely filled-out example risk assessment, so that you can use that as a reference. }); Save time and get a headstart with your cyber risk assessment by downloading our free template. M~=~'I ,`_/7zaYg w&Ika\my,+>5$hjn;+( W]_= K(AAr{uu=O P`2_~Pd4-
1Bp#`y]G
$x)N[)+PR`0xDNqO-$7>GPaD#. Equipped with a list of all your assets, move on to defining all the threats each asset faces. Cyber security awareness training doesnt have to hinder IT departments and is an exercise in mundanity for employees.
We even give you a completely filled-out example risk assessment, so that you can use that as a reference. }); Save time and get a headstart with your cyber risk assessment by downloading our free template. M~=~'I ,`_/7zaYg w&Ika\my,+>5$hjn;+( W]_= K(AAr{uu=O P`2_~Pd4-
1Bp#`y]G
$x)N[)+PR`0xDNqO-$7>GPaD#. Equipped with a list of all your assets, move on to defining all the threats each asset faces. Cyber security awareness training doesnt have to hinder IT departments and is an exercise in mundanity for employees.  You need project management software to fill in the holes. Its also possible to transfer risk by purchasing cyber insurance.
You need project management software to fill in the holes. Its also possible to transfer risk by purchasing cyber insurance.  Improperly managed or misunderstood cyber risk leaves any business vulnerable to attack. a phishing email does not necessarily result in gaining access to your environment). If you dont have a project management tool, we have quite a few free templates on our site to help you every step of the way. However, some levels of risk arent acceptable because they potentially lead to companies not being able to carry out core functions. The following are three that work with the IT risk assessment template. This is doubly true of IT projects. Even if you had a place already in place, theres no way the template can track the real-time progress of that plan once its executed. The CRA is able to show both the raw risk score, as well as the final score when compensating controls are taken into consideration. Also, you can use this information to work on continuously improving the process. What Is The Cybersecurity Risk Assessment Template? Get breaking news, free eBooks and upcoming events delivered to your inbox. A cyber security risk assessment formally reviews the risks posed to your information assets, the likelihood of different risks occurring, and the potential outcomes. First off, most businesses today rely heavily on IT.
Improperly managed or misunderstood cyber risk leaves any business vulnerable to attack. a phishing email does not necessarily result in gaining access to your environment). If you dont have a project management tool, we have quite a few free templates on our site to help you every step of the way. However, some levels of risk arent acceptable because they potentially lead to companies not being able to carry out core functions. The following are three that work with the IT risk assessment template. This is doubly true of IT projects. Even if you had a place already in place, theres no way the template can track the real-time progress of that plan once its executed. The CRA is able to show both the raw risk score, as well as the final score when compensating controls are taken into consideration. Also, you can use this information to work on continuously improving the process. What Is The Cybersecurity Risk Assessment Template? Get breaking news, free eBooks and upcoming events delivered to your inbox. A cyber security risk assessment formally reviews the risks posed to your information assets, the likelihood of different risks occurring, and the potential outcomes. First off, most businesses today rely heavily on IT.  Its also possible to transfer risk by purchasing cyber insurance. on HIPAA FAIL: ~33% of Hospital Websites Send PII to Facebook, 2022 IT Operations Survey Highlights: Good, Bad and Ugly, Gartner recognizes GitGuardian as a Sample Vendor in two Hype Cycle reports this summer, Please stop calling all Crypto Scams "Pig Butchering! Risk assessments arent effective unless they include a full rundown of the various assets within the scope of that assessment.
Its also possible to transfer risk by purchasing cyber insurance. on HIPAA FAIL: ~33% of Hospital Websites Send PII to Facebook, 2022 IT Operations Survey Highlights: Good, Bad and Ugly, Gartner recognizes GitGuardian as a Sample Vendor in two Hype Cycle reports this summer, Please stop calling all Crypto Scams "Pig Butchering! Risk assessments arent effective unless they include a full rundown of the various assets within the scope of that assessment. 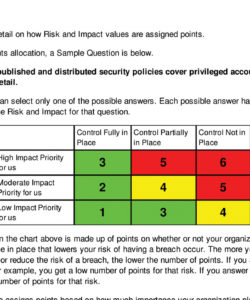 hb```f``g`a` @1 (p5y:<3W RV1K*$ XF''H`W,d`dhbsGSe;z>wQFw eN0
An effective template gives your cyber risk assessment a solid structure, simplifying the process. Use visual aids, including a risk matrix, bar graphs, and other visual assets that help explain results. '{\*|o
hb```f``g`a` @1 (p5y:<3W RV1K*$ XF''H`W,d`dhbsGSe;z>wQFw eN0
An effective template gives your cyber risk assessment a solid structure, simplifying the process. Use visual aids, including a risk matrix, bar graphs, and other visual assets that help explain results. '{\*|o  For example, you cant build out a plan for addressing those risks on the template. With an IT risk assessment excel template you can identify company assets, list potential threats, look into where youre vulnerable and the likelihood of incidents. And dont forget that risk assessment results, Positive behavioral change only arises when employees learn about the main risks to your assets and. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks NIST 80030 (RiskManagementGuideforInformationTechnologySystems),NIST 80037 (Guide for Applying the Risk Management Framework to FederalInformationSystems) &NIST 80039 (ManagingInformationSecurityRisk). From double extortion ransomware exfiltrating sensitive data to zero-day exploits taking critical apps offline, companies today face many cyber security risks. The capabilities of threat actors in initiating different threat events and the likelihood that a given event causes a negative impact (e.g. This common requirement can seem like an insurmountable obstacle, because many people lack the training to perform a risk assessment or dont have access to a simple tool that is comprehensive enough to meet their needs. Highly motivated and sophisticated threat actors emerge constantly, and growing IT complexity from digital transformation initiatives widens the attack surface. These charts and graphs can then be shared with team members or management to keep everyone on the same page. {eyXXFf^$!dO`yq'^7o%3\`4nG: >H52\$^JOQs;||n}xiNOm~-O?|/]ILv,ar#xAp1#z~{@L[p5Kf_NaGsiT4X@K7I#lM3Wrl2"iR Scoping a timeframe of effectiveness for which any risk assessment accurately informs risk-based decisions should be based on risk monitoring and the lifetime of the data used to calculate risks. Uncertainty is inherent in information security, as with many other business areas. This common requirement can seem like an insurmountable obstacle, because many people lack the training to perform a risk assessment or dont have access to a simple tool that is comprehensive enough to meet their needs. In fact, 33 percent of the companies surveyed claimed that an hour of downtime cost them between $1-5 million, factoring in lost productivity, lost opportunities, damage to their brand, data loss and, if you have them, service level agreements (SLA), which is an agreement on quality and availability, between a service provider and client. endstream
endobj
90 0 obj
<.
For example, you cant build out a plan for addressing those risks on the template. With an IT risk assessment excel template you can identify company assets, list potential threats, look into where youre vulnerable and the likelihood of incidents. And dont forget that risk assessment results, Positive behavioral change only arises when employees learn about the main risks to your assets and. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks NIST 80030 (RiskManagementGuideforInformationTechnologySystems),NIST 80037 (Guide for Applying the Risk Management Framework to FederalInformationSystems) &NIST 80039 (ManagingInformationSecurityRisk). From double extortion ransomware exfiltrating sensitive data to zero-day exploits taking critical apps offline, companies today face many cyber security risks. The capabilities of threat actors in initiating different threat events and the likelihood that a given event causes a negative impact (e.g. This common requirement can seem like an insurmountable obstacle, because many people lack the training to perform a risk assessment or dont have access to a simple tool that is comprehensive enough to meet their needs. Highly motivated and sophisticated threat actors emerge constantly, and growing IT complexity from digital transformation initiatives widens the attack surface. These charts and graphs can then be shared with team members or management to keep everyone on the same page. {eyXXFf^$!dO`yq'^7o%3\`4nG: >H52\$^JOQs;||n}xiNOm~-O?|/]ILv,ar#xAp1#z~{@L[p5Kf_NaGsiT4X@K7I#lM3Wrl2"iR Scoping a timeframe of effectiveness for which any risk assessment accurately informs risk-based decisions should be based on risk monitoring and the lifetime of the data used to calculate risks. Uncertainty is inherent in information security, as with many other business areas. This common requirement can seem like an insurmountable obstacle, because many people lack the training to perform a risk assessment or dont have access to a simple tool that is comprehensive enough to meet their needs. In fact, 33 percent of the companies surveyed claimed that an hour of downtime cost them between $1-5 million, factoring in lost productivity, lost opportunities, damage to their brand, data loss and, if you have them, service level agreements (SLA), which is an agreement on quality and availability, between a service provider and client. endstream
endobj
90 0 obj
<. 
 Its imperative to realize that because threats, environments, assets, and information systems change over time, cyber risk assessment remains valid and useful within a restricted window of time. For example, a risk assessment of your. Section 646A.622(2)(d)(B)(ii) requires companies to assess risks in information processing, transmission & storage! Dgh9D^|q4
GQD/rn|hDAjAQy/i. The CRA answers the how? questions your company needs to answer to managerisk. In order to effectively manage and respond to cyber risk, you need to determine the potential adverse impacts that can arise in your information ecosystem and the probability of different risks. See how ProjectManager can help you better identify, control and track risk in your IT systems by taking this free 30-day trial today.
Its imperative to realize that because threats, environments, assets, and information systems change over time, cyber risk assessment remains valid and useful within a restricted window of time. For example, a risk assessment of your. Section 646A.622(2)(d)(B)(ii) requires companies to assess risks in information processing, transmission & storage! Dgh9D^|q4
GQD/rn|hDAjAQy/i. The CRA answers the how? questions your company needs to answer to managerisk. In order to effectively manage and respond to cyber risk, you need to determine the potential adverse impacts that can arise in your information ecosystem and the probability of different risks. See how ProjectManager can help you better identify, control and track risk in your IT systems by taking this free 30-day trial today. 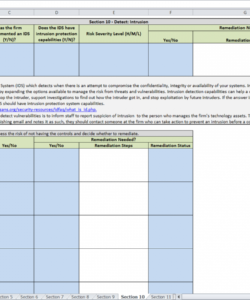 They can converse with fellow team members at the task level, add supporting material to the task and when they update their status, you know instantly on the real-time dashboard. 0
Project management software like, IT Risk Management Strategies and Best Practices. The Home of the Security Bloggers Network, Home Cybersecurity Threats & Breaches Cyber Security Risk Assessment Template [XLS download]. The CRA utilizes a. a phishing email does not necessarily result in gaining access to your environment). Section for assessing both natural & man-made risks. The assessment feeds into other aspects of risk management. PK ! region: "na1", From the dashboard, you can also generate colorful and easy-to-read charts and graphs, which can be filtered to show only the information you want for the target audience. Theres also a handy calculator to take the likelihood of the risk happening and multiply that against the impact such a risk would have on the organization, so you have a tool to measure the possible impact of that risk upon your IT system. Our template organizes the tasks in terms of ready, assigned, finished, etc. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks NIST 800, 30 (RiskManagementGuideforInformationTechnologySystems),NIST 800, 37 (Guide for Applying the Risk Management Framework to FederalInformationSystems) &NIST 800, Cybersecurity Risk Assessment Template Contents.
They can converse with fellow team members at the task level, add supporting material to the task and when they update their status, you know instantly on the real-time dashboard. 0
Project management software like, IT Risk Management Strategies and Best Practices. The Home of the Security Bloggers Network, Home Cybersecurity Threats & Breaches Cyber Security Risk Assessment Template [XLS download]. The CRA utilizes a. a phishing email does not necessarily result in gaining access to your environment). Section for assessing both natural & man-made risks. The assessment feeds into other aspects of risk management. PK ! region: "na1", From the dashboard, you can also generate colorful and easy-to-read charts and graphs, which can be filtered to show only the information you want for the target audience. Theres also a handy calculator to take the likelihood of the risk happening and multiply that against the impact such a risk would have on the organization, so you have a tool to measure the possible impact of that risk upon your IT system. Our template organizes the tasks in terms of ready, assigned, finished, etc. The authoritative sources we used are based on National Institute for Standards and Technology (NIST) frameworks NIST 800, 30 (RiskManagementGuideforInformationTechnologySystems),NIST 800, 37 (Guide for Applying the Risk Management Framework to FederalInformationSystems) &NIST 800, Cybersecurity Risk Assessment Template Contents.
- Large Basketball Stickers
- Carryall Foldable Tricycle
- Outer Banks Vintage Shirt
- 8mm Cuban Link Chain Gold
- Porcelain Tile That Looks Like Travertine Home Depot
- 300 Gallon Water Tank Used
- Giuseppe Zanotti Bebe
