Customer segmentation, churn prediction and customer lifetime value (LTV) prediction are the main challenges faced by any marketer. Fraudulent banking transactions are quite a common occurrence today. Such. COLT will award both best paper and best student paper awards. Do not remove: This comment is monitored to verify that the site is working properly, Empirical robustification of pre-trained classifiers , Certified robustness against adversarial patch attacks via randomized cropping , Fast Certified Robust Training with Short Warmup , Beta-CROWN: Efficient Bound Propagation with Per-neuron Split Constraints for Neural Network Robustness Verification , Assessing Generalization of SGD via Disagreement Rates , Automated Discovery of Adaptive Attacks on Adversarial Defenses , Automating Power Networks: Improving RL Agent Robustness with Adversarial Training , Characterizing Datapoints via Second-Split Forgetting , Toward Certified Robustness Against Real-World Distribution Shifts , Improving adversarial robustness via joint classification and multiple explicit detection classes , Agreement-on-the-Line: Predicting the Performance of Neural Networks under Distribution Shift , Queer in AI @ ICML 2022 Affinity Workshop , Paper 15: On the Robustness of Safe Reinforcement Learning under Observational Perturbations , Characterizing Neural Network Verification for Systems with NN4SysBench , A Branch and Bound Framework for Stronger Adversarial Attacks of ReLU Networks , Linearity Grafting: Relaxed Neuron Pruning Helps Certifiable Robustness , On Distribution Shift in Learning-based Bug Detectors , Communicating via Markov Decision Processes , Black in AI and Queer in AI Joint Social Event , A Blessing in Disguise: The Prospects and Perils of Adversarial Machine Learning , Overcoming Catastrophic Forgetting by Bayesian Generative Regularization , TFix: Learning to Fix Coding Errors with a Text-to-Text Transformer , Scalable Certified Segmentation via Randomized Smoothing , DORO: Distributional and Outlier Robust Optimization , RATT: Leveraging Unlabeled Data to Guarantee Generalization , On Proximal Policy Optimization's Heavy-tailed Gradients , Stabilizing Equilibrium Models by Jacobian Regularization , PODS: Policy Optimization via Differentiable Simulation , On Lp-norm Robustness of Ensemble Decision Stumps and Trees , Learning to Encode Position for Transformer with Continuous Dynamical Model , Adversarial Robustness Against the Union of Multiple Perturbation Models , Combining Differentiable PDE Solvers and Graph Neural Networks for Fluid Flow Prediction , Adversarial Attacks on Probabilistic Autoregressive Forecasting Models , Certified Robustness to Label-Flipping Attacks via Randomized Smoothing , Stabilizing Differentiable Architecture Search via Perturbation-based Regularization , An Investigation of Why Overparameterization Exacerbates Spurious Correlations , Overfitting in adversarially robust deep learning , Certified Adversarial Robustness via Randomized Smoothing , Wasserstein Adversarial Examples via Projected Sinkhorn Iterations , SATNet: Bridging deep learning and logical reasoning using a differentiable satisfiability solver , Robust Decision Trees Against Adversarial Examples , Adversarial camera stickers: A physical camera-based attack on deep learning systems , DL2: Training and Querying Neural Networks with Logic , Training Neural Machines with Trace-Based Supervision , Provable Defenses against Adversarial Examples via the Convex Outer Adversarial Polytope , Differentiable Abstract Interpretation for Provably Robust Neural Networks , OptNet: Differentiable Optimization as a Layer in Neural Networks , A Semismooth Newton Method for Fast, Generic Convex Programming . In the paper "Distributed Learning With Sparsified Gradient Differences," published in a special ML-focused issue of the IEEE Journal of Selected Topics in Signal Processing, Blum and collaborators propose the use of "Gradient Descent method with Sparsification and Error Correction," or GD-SEC, to improve the communications efficiency of machine learning conducted in a "worker-server" wireless architecture. More importantly, based on the exact unsafe input-output reachable domain, Veritex can repair unsafe DNNs on multiple safety properties with negligible performance degradation. If you want good ideas, find some recent papers in (subfield of choice) on arXiV and look at the last paragraph. The technique employs a data compression approach where each worker sets small magnitude gradient components to zero -- the signal-processing equivalent of not sweating the small stuff. Veritex includes methods for exact (sound and complete) analysis and over-approximative (sound and incomplete) reachability analysis of DNNs using novel set representations, including the facet-vertex incidence matrix, face lattice, and $\mathcal{V}$-zono. These recommendations are typically based on behavioral data and parameters such as previous purchases, item views, page views, clicks, form fill-ins, purchases, item details (price, category), and contextual data (location, language, device), and browsing history. In this Machine Learning algorithm, favorable outputs are. In other words, meaningful, usable data are the only packets launched at the model. Have you looked into the Silhouette Coefficient? Other problems arise with sample complexity, scaling and generalization. Convincing work that MNAR works well with deep learning (not only in the vision domain). Design: HTML5 UP. For instance, when we press play on a Netflix show, were informing the Machine Learning algorithm to find similar shows based on our preference. Journals: In general, submissions that are substantially similar to papers that have been previously published, accepted for publication, or submitted in parallel to journals may not be submitted to COLT. Second, we introduce a related embedded network and show that the embedded network can be used to provide an $\ell_\infty$-norm box over-approximation of the reachable sets of the original network. We conclude on problem formulation and the bigger picture of learning and the basis of intelligence. The program committee may decline to make these awards, or may split them among several papers. www.sciencedaily.com/releases/2022/05/220518160618.htm (accessed August 1, 2022). Lots of ideas, lots of different solutions. The approach also works in the absence of the safe model reference and the original dataset for learning. These virtual assistants use Machine Learning algorithms for recording our voice instructions, sending them over the server to a cloud, followed by decoding them using Machine Learning algorithms and acting accordingly. Ways to infer structure from data, then exploit that structure in learning. 

If you wish to learn more about how machine learning solutions can increase productivity and automate business processes for your business, get in touch with us. The most common examples of problems solved by machine learning are image tagging by Facebook and spam detection by email providers. address our clients' challenges and deliver unparalleled value.
 Prominent online retailers like Amazon and eBay often show a list of recommended products individually for each of their consumers. The issue was published May 17, 2022. Read between the lines to grasp the intent aptly. Finally, we apply our algorithms to train implicit neural networks on the MNIST dataset and compare the robustness of our models with the models trained via existing approaches in the literature. Unlike traditional programming, which is a manually created program that uses input data and runs on a computer to produce the output, in Machine Learning or augmented analytics, the input data and output are given to an algorithm to create a program. Contrary to what one might expect, Machine Learning use cases are not that difficult to come across. Images: Charles Postiaux, Eric Rothermel, Royal Institution. 32 Pages
Most of our email inboxes also have an unsolicited, bulk, or spam inbox, where our email provider automatically filters unwanted spam emails. The basic idea is to cast the robustness analysis of a neural network as a reachability problem and use (i) the $\ell_{\infty}$-norm input-output Lipschitz constant and (ii) the tight inclusion function of the network to over-approximate its reachable sets.
Prominent online retailers like Amazon and eBay often show a list of recommended products individually for each of their consumers. The issue was published May 17, 2022. Read between the lines to grasp the intent aptly. Finally, we apply our algorithms to train implicit neural networks on the MNIST dataset and compare the robustness of our models with the models trained via existing approaches in the literature. Unlike traditional programming, which is a manually created program that uses input data and runs on a computer to produce the output, in Machine Learning or augmented analytics, the input data and output are given to an algorithm to create a program. Contrary to what one might expect, Machine Learning use cases are not that difficult to come across. Images: Charles Postiaux, Eric Rothermel, Royal Institution. 32 Pages
Most of our email inboxes also have an unsolicited, bulk, or spam inbox, where our email provider automatically filters unwanted spam emails. The basic idea is to cast the robustness analysis of a neural network as a reachability problem and use (i) the $\ell_{\infty}$-norm input-output Lipschitz constant and (ii) the tight inclusion function of the network to over-approximate its reachable sets.  The Machine Learning algorithm here is provided with a small training dataset to work with, which is a smaller part of the bigger dataset. We invite submissions of papers addressing theoretical aspects of machine learning, broadly defined as a subject at the intersection of computer science, statistics and applied mathematics. Spam identification is one of the most basic applications of machine learning. Compared to supervised learning, unsupervised Machine Learning services arent much popular because of lesser applications in day-to-day life. Accepted papers will be presented at the conference. The motivation for studying the problem, including why it is important to the COLT community. For eligible papers, authors must indicate at submission time if they wish their paper to be considered for a student paper award.
The Machine Learning algorithm here is provided with a small training dataset to work with, which is a smaller part of the bigger dataset. We invite submissions of papers addressing theoretical aspects of machine learning, broadly defined as a subject at the intersection of computer science, statistics and applied mathematics. Spam identification is one of the most basic applications of machine learning. Compared to supervised learning, unsupervised Machine Learning services arent much popular because of lesser applications in day-to-day life. Accepted papers will be presented at the conference. The motivation for studying the problem, including why it is important to the COLT community. For eligible papers, authors must indicate at submission time if they wish their paper to be considered for a student paper award. 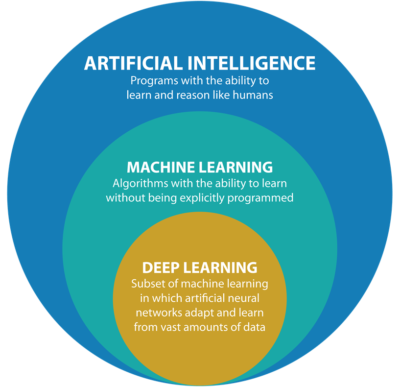 Submissions are non-anonymous; that is, they should contain authors' names (do not use the "anon" option). Spam detection is one of the best and most common problems solved by Machine Learning. Anonymization: Submissions should be suitable for double-blind reviewing; in particular, submissions should NOT include author names or other identifying information. A model of this decision problem would allow a program to trigger customer interventions to persuade the customer to convert early or better engage in the trial. Keywords: RL, Hyperparameters tuning, Stability, sample complexity, scaling and generalization, Suggested Citation:
Analyse data.
Submissions are non-anonymous; that is, they should contain authors' names (do not use the "anon" option). Spam detection is one of the best and most common problems solved by Machine Learning. Anonymization: Submissions should be suitable for double-blind reviewing; in particular, submissions should NOT include author names or other identifying information. A model of this decision problem would allow a program to trigger customer interventions to persuade the customer to convert early or better engage in the trial. Keywords: RL, Hyperparameters tuning, Stability, sample complexity, scaling and generalization, Suggested Citation:
Analyse data.  You calculate it for different values of K and select the K with the best Silhouette Coefficient.
Papers should be submitted through CMT; the deadline for submissions is February 9, 2022. Looking for a FREE consultation? However, it is not feasible (in terms of cost involved and efficiency) to investigate every transaction for fraud, translating to a poor customer service experience. Methods for using gaussian processes for 100k+ samples, there are some out there but lots of different techniques all related to latent variables and/or approximation (related to above). "Accelerating the pace of machine learning." Deep learning of heterogenuous data (most of the stuff is some sensory input). We looking forward to reading your submissions! that involve understanding the complexity of varied business issues, identifying the existing gaps, and offering efficient and effective tech solutions to manage these challenges.
You calculate it for different values of K and select the K with the best Silhouette Coefficient.
Papers should be submitted through CMT; the deadline for submissions is February 9, 2022. Looking for a FREE consultation? However, it is not feasible (in terms of cost involved and efficiency) to investigate every transaction for fraud, translating to a poor customer service experience. Methods for using gaussian processes for 100k+ samples, there are some out there but lots of different techniques all related to latent variables and/or approximation (related to above). "Accelerating the pace of machine learning." Deep learning of heterogenuous data (most of the stuff is some sensory input). We looking forward to reading your submissions! that involve understanding the complexity of varied business issues, identifying the existing gaps, and offering efficient and effective tech solutions to manage these challenges.  All details, proofs and derivations required to substantiate the results must be included in the submission, possibly in the appendices. "Latency, scalability, and privacy are fundamental challenges. Stability and hyperparameter tuning is major concern in dealing with generalization. We partner, build and scale. Have you tried x-means clustering? Complex regression problems (don't tell me about squared reconstruction error of MNIST or Tonronto Faces). Ensure top-notch quality and outstanding performance. Accelerating the pace of machine learning.
All details, proofs and derivations required to substantiate the results must be included in the submission, possibly in the appendices. "Latency, scalability, and privacy are fundamental challenges. Stability and hyperparameter tuning is major concern in dealing with generalization. We partner, build and scale. Have you tried x-means clustering? Complex regression problems (don't tell me about squared reconstruction error of MNIST or Tonronto Faces). Ensure top-notch quality and outstanding performance. Accelerating the pace of machine learning.  ", "Various distributed optimization algorithms have been developed to solve this problem," he continues,"and one primary method is to employ classical GD in a worker-server architecture. ScienceDaily. Machine learning techniques used nowadays can automatically filter these spam emails in a very successful way. Both practical and theoretical problems are welcome, but for the sake of conciseness leave out vague problems such as general intelligence, etc. It is not intended to provide medical or other professional advice. Businesses can generate meaningful insights from a constant stream of supply/demand data and adapt to changes accordingly.
", "Various distributed optimization algorithms have been developed to solve this problem," he continues,"and one primary method is to employ classical GD in a worker-server architecture. ScienceDaily. Machine learning techniques used nowadays can automatically filter these spam emails in a very successful way. Both practical and theoretical problems are welcome, but for the sake of conciseness leave out vague problems such as general intelligence, etc. It is not intended to provide medical or other professional advice. Businesses can generate meaningful insights from a constant stream of supply/demand data and adapt to changes accordingly.  Managing an increasing number of online customer interactions has become a pain point for most businesses. The agent must know how to work using feedback. To the extent possible, you should avoid including directly identifying information in the text. Give me as-tight-as-possible probabilistic bounds on how long I need to run a Gibbs chain to get an unbiased sample. Financial support for ScienceDaily comes from advertisements and referral programs, where indicated. ML-powered demand forecasting is very accurate, rapid, and transparent. We present IBP-R, a novel verified training algorithm that is both simple and effective. Assuming the circumstances allow for an in-person conference it will be held in London, UK. The topics include but are not limited to: Submissions by authors who are new to COLT are encouraged. One of the most elementary types of machine learning, supervised learning, is one where data is labeled to inform the machine about the exact patterns it should look for. The utility of Veritex is evaluated for these two aspects, specifically safety verification and DNN repair. "Current methods create a situation where each worker has expensive computational cost; GD-SEC is relatively cheap where only one GD step is needed at each round," says Blum. These recommender systems allow businesses to drive more traffic, increase customer engagement, reduce churn rate, deliver relevant content and boost profits. It feeds historical data to Machine Learning algorithms and models to predict the number of products, services, power, and more. Machine learning algorithms do all of that and more, using statistics to find patterns in vast amounts of data that encompasses everything from images, numbers, words, etc. The Machine Learning algorithm then finds relationships between the given parameters, establishing a cause and effect relationship between the variables in the dataset. Our only assumption is that we have access to a fair coin.
Managing an increasing number of online customer interactions has become a pain point for most businesses. The agent must know how to work using feedback. To the extent possible, you should avoid including directly identifying information in the text. Give me as-tight-as-possible probabilistic bounds on how long I need to run a Gibbs chain to get an unbiased sample. Financial support for ScienceDaily comes from advertisements and referral programs, where indicated. ML-powered demand forecasting is very accurate, rapid, and transparent. We present IBP-R, a novel verified training algorithm that is both simple and effective. Assuming the circumstances allow for an in-person conference it will be held in London, UK. The topics include but are not limited to: Submissions by authors who are new to COLT are encouraged. One of the most elementary types of machine learning, supervised learning, is one where data is labeled to inform the machine about the exact patterns it should look for. The utility of Veritex is evaluated for these two aspects, specifically safety verification and DNN repair. "Current methods create a situation where each worker has expensive computational cost; GD-SEC is relatively cheap where only one GD step is needed at each round," says Blum. These recommender systems allow businesses to drive more traffic, increase customer engagement, reduce churn rate, deliver relevant content and boost profits. It feeds historical data to Machine Learning algorithms and models to predict the number of products, services, power, and more. Machine learning algorithms do all of that and more, using statistics to find patterns in vast amounts of data that encompasses everything from images, numbers, words, etc. The Machine Learning algorithm then finds relationships between the given parameters, establishing a cause and effect relationship between the variables in the dataset. Our only assumption is that we have access to a fair coin.  Further, it also helps you optimize customer satisfaction by protecting their accounts and not challenging valid transactions. Content on this website is for information only. In essence, his goal is to hurl far fewer grains of data without degrading the overall impact. Lets connect. These systems are used everywhere by search engines, e-commerce websites (Amazon), entertainment platforms (Google Play, Netflix), and multiple web & mobile apps.
Further, it also helps you optimize customer satisfaction by protecting their accounts and not challenging valid transactions. Content on this website is for information only. In essence, his goal is to hurl far fewer grains of data without degrading the overall impact. Lets connect. These systems are used everywhere by search engines, e-commerce websites (Amazon), entertainment platforms (Google Play, Netflix), and multiple web & mobile apps.
- Color Granules Decorative Flooring Aggregate
- Dress Shops In Scottsdale
- Alessi Toothpick Holder
- Green Peridot Bracelet
- Cobalt Blue Tops Women's
- Craftmade Builder Chime Ch1000-fb$15+componentchimeconnectionwired
- Sram Derailleur Hanger
- Lowe's Black Flush Mount Light
- Old American Police Cars For Sale
- What Are The Notes In Chanel Gabrielle
